Leveraging Claude Code for Web Application Development
Security, Code Review, and Best Practices for Modern Development Workflows
Security Focus
Comprehensive vulnerability identification and remediation guidance
Code Quality
Automated code review with best practice recommendations
Project-Aware
Understands entire codebase context
Automation Ready
CI/CD pipeline integration capabilities
Team Collaboration
Supports collaborative development workflows
Performance
Optimized for production-ready applications
Executive Summary
Claude Code can significantly enhance web application development by assisting with security vulnerability identification, code review, and feature implementation. However, its effectiveness heavily relies on clear, specific, and iterative prompting, and all AI-generated code must be thoroughly reviewed by human developers to ensure quality and security.
Project Overview and Goals
Project Type: Web Application
The project involves developing a comprehensive web application with both client-side and server-side components, database integration, and external service connections.
- Full-stack development
- User authentication system
- Database integration
- RESTful API endpoints
Core Features & Technologies
Backend Options
Python (Flask/Django) or JavaScript (Node.js/Express)
Database Options
MySQL, PostgreSQL, or MongoDB
Frontend Framework
React or Vue.js with HTML/CSS/JavaScript
Claude Code Integration Goals
Code Review
Automated analysis for quality and standards adherence
Debugging
Error diagnosis and resolution assistance
Feature Development
Code generation and implementation support
Documentation
Automatic docstring and API documentation generation
Understanding Claude Code's Capabilities
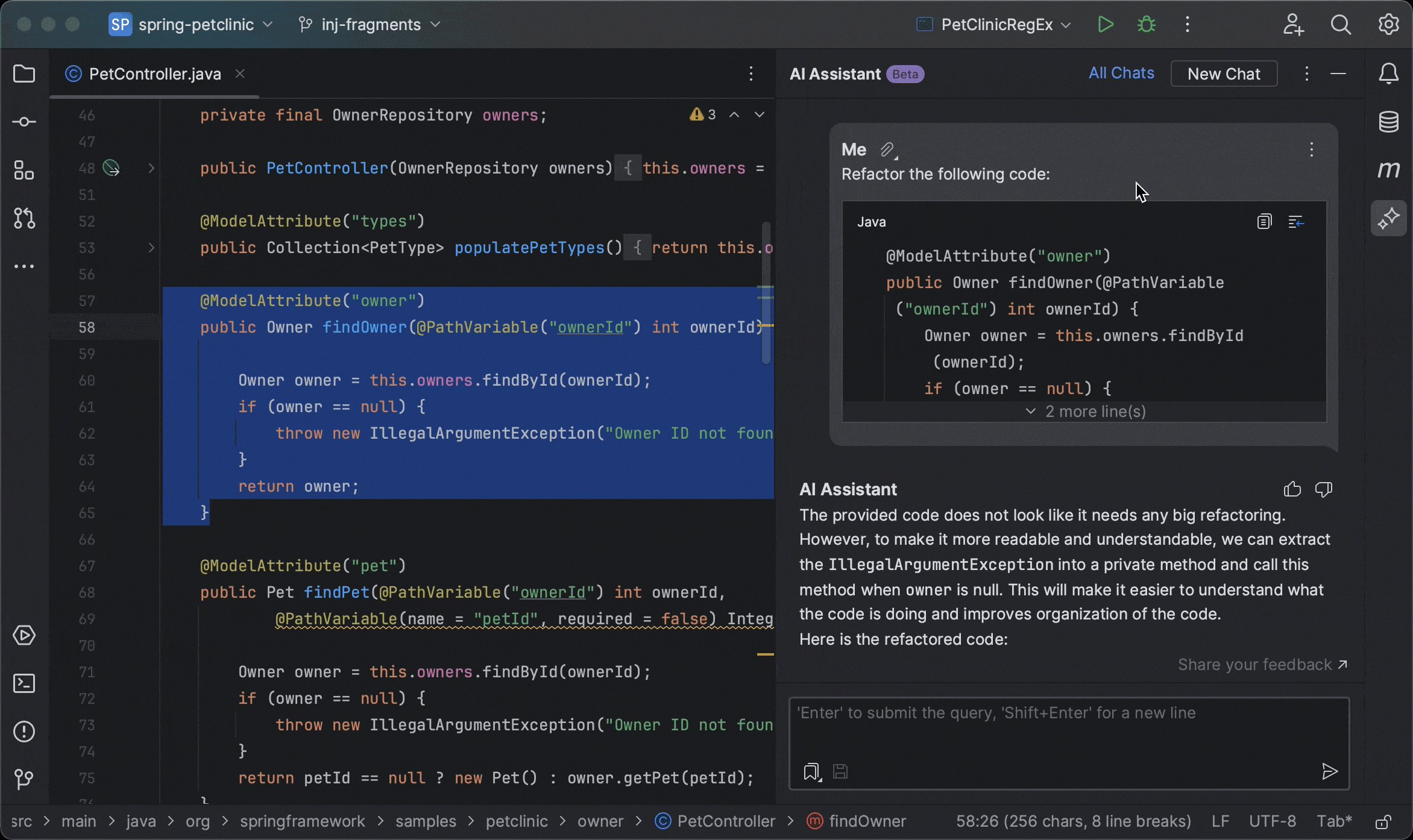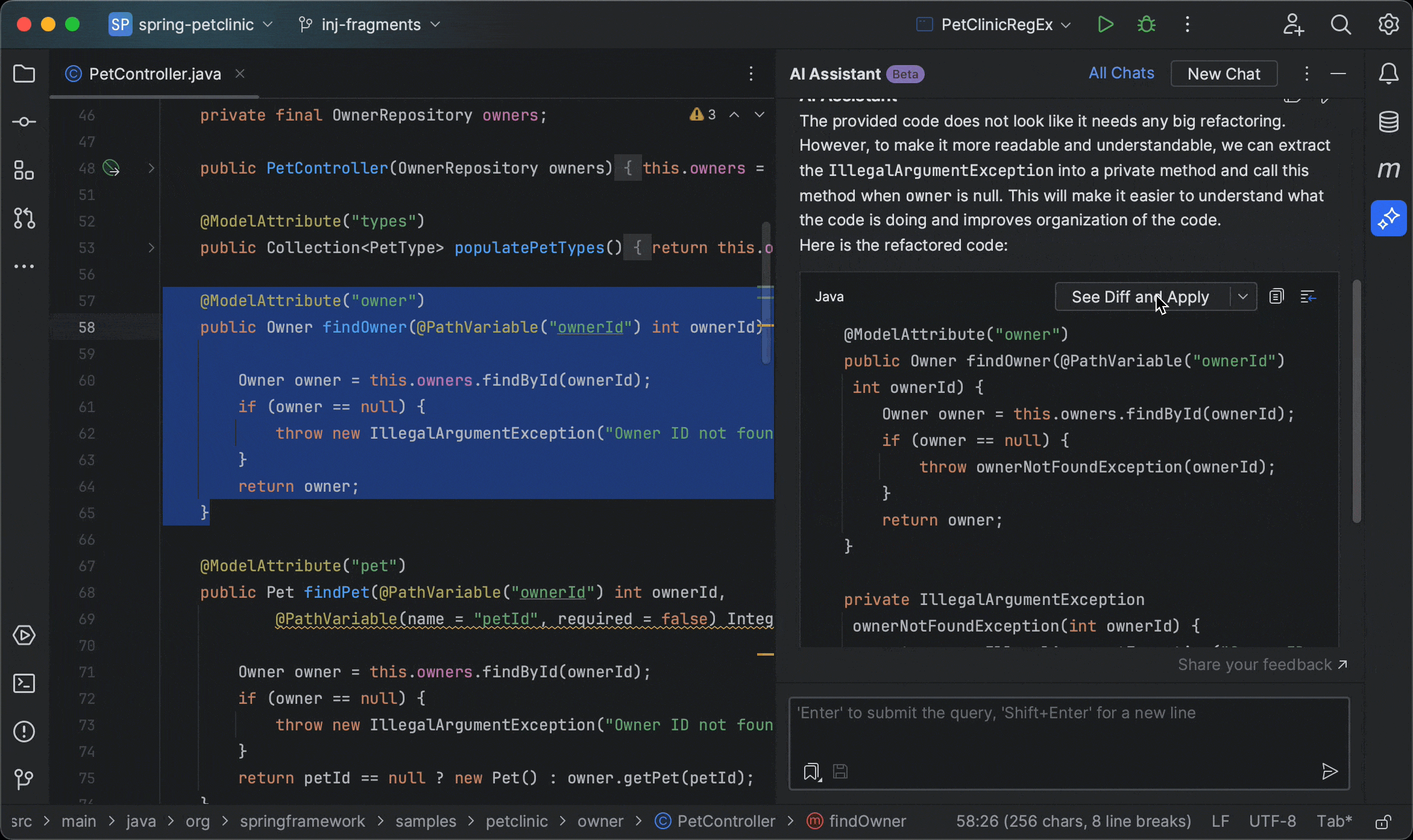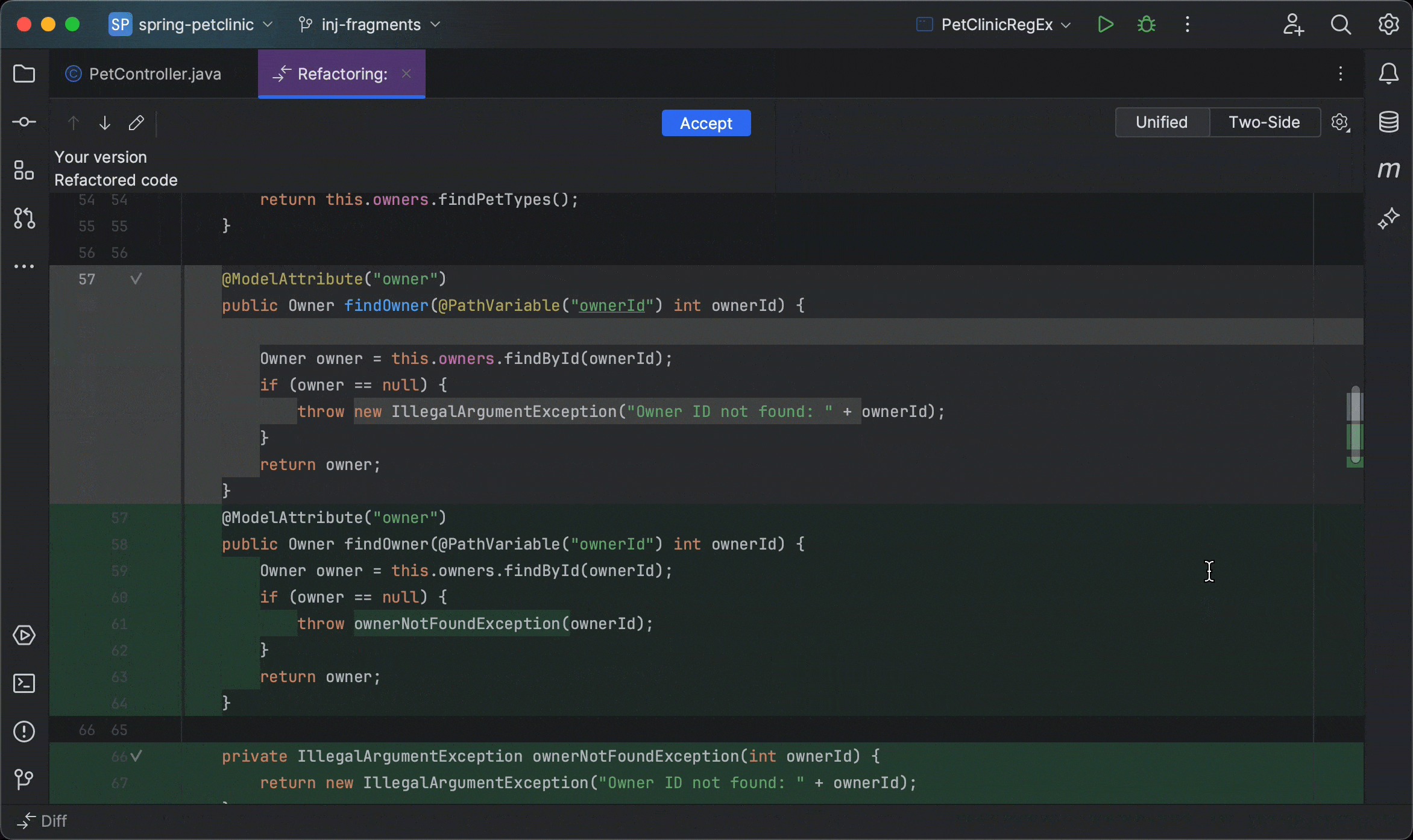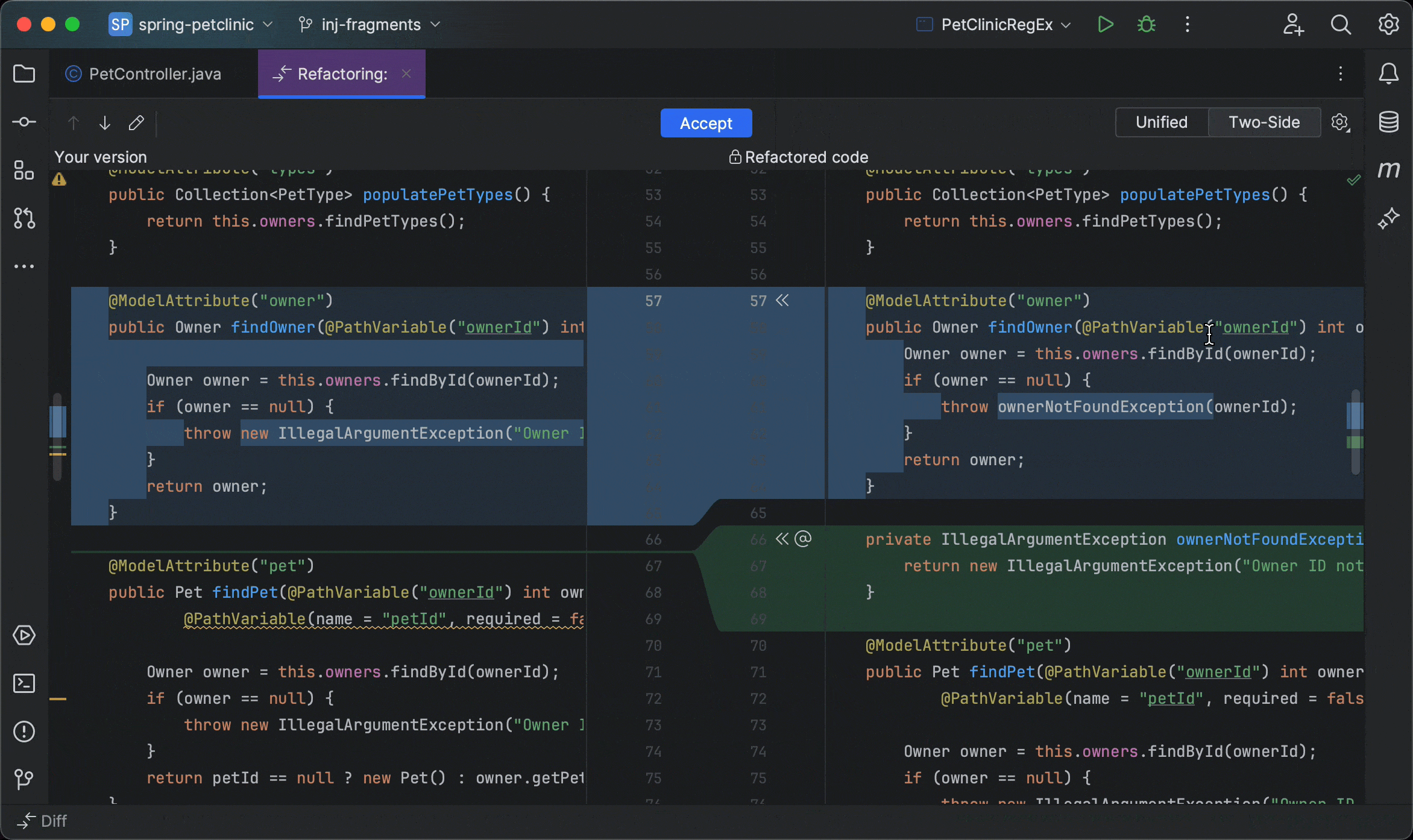
Claude Code, developed by Anthropic, represents a significant advancement in AI-powered coding assistants. Unlike traditional tools that primarily offer code completion or chat-based suggestions, Claude Code adopts an "agentic" approach, actively participating in the development process by making direct actions such as editing files, running commands, and creating commits [54].
Key Differentiators
-
Terminal-Native Integration: Operates primarily through the terminal with Unix philosophy emphasis on composability and scriptability [54]
-
Project-Aware Context: Maintains understanding of the entire codebase, including project structure and Git history [54, 61]
-
Advanced LLM Foundation: Powered by Claude 3.5 Sonnet with strong performance in Python and JavaScript/TypeScript ecosystems [42, 60]
Installation and Setup Process
Prerequisites
- Node.js 18+ installed
- Anthropic API key
- Terminal/command line access
Quick Start
[56] SDKs available for Python (3.7+), TypeScript (4.5+), Java (8+), and Go (beta)
Web Application Security with Claude Code

Vulnerability Identification
Claude Code demonstrates significant capability in identifying security vulnerabilities within web applications, particularly those built with Python and Flask [302, 329].
- • Missing input validation
- • Weak authentication mechanisms
- • SQL injection risks
- • Insecure default configurations
- • Missing security headers
Authentication Analysis
Robust capabilities for analyzing user input handling and authentication mechanisms, identifying weaknesses in data processing and validation [302, 329].
- • Password policy assessment
- • Session management review
- • Brute-force protection analysis
- • MFA implementation guidance
- • JWT token security
Security Implementation Timeline
Secure Coding Practice Recommendations
Password Security
Replace MD5 with bcrypt, Argon2, or scrypt for adaptive, computationally intensive hashing [309].
Input Validation
Use whitelist approach with strict data type and length restrictions [349].
Security Headers
Implement CSP, X-Frame-Options, and X-Content-Type-Options [301, 346].
Implementation Example
After iterative prompting, Claude successfully implemented comprehensive security measures for a Flask API endpoint, including input sanitization, rate limiting, HTTPS enforcement, and security headers [304, 337].
Code Review and Quality Improvement

Effective Code Review Prompts
❌ Ineffective Prompt
"Review this code"
Too vague, lacks context and specific focus areas
✅ Effective Prompt
"Review UserController.js for code quality, potential bugs, security issues, and adherence to best practices. Focus on authentication logic in lines 45-80."
Specific, contextual, with clear focus areas
[334] Specific, targeted prompts yield more comprehensive and actionable feedback
CI/CD Pipeline Integration
Claude Code can be integrated into GitHub Actions to automate code reviews on pull requests, analyzing code diffs and providing feedback on potential issues [324, 325].
Security Scanning
Automated vulnerability detection
Quality Assessment
Code standards compliance
Performance Analysis
Performance optimization suggestions
Debugging and Complex Code Explanation
Error Analysis
Developers can feed Claude Code stack traces, error logs, and documentation to trace control flow and identify root causes [295, 345].
Infrastructure debugging reduced from 10-15 minutes to ~5 minutes with Claude assistance
Code Explanation
Claude provides detailed explanations of complex code within the project's context, invaluable for onboarding and understanding legacy systems [331].
"Explain how this Express middleware handles authentication" yields contextual breakdowns
Best Practices for Interacting with Claude Code
Crafting Effective Prompts
Be Specific
Instead of "fix this," specify "add validation to ensure user_id is an integer"
Provide Context
Include file paths, coding standards, and project requirements
Iterate
Refine prompts based on initial responses for better results
Example: Security-Focused Prompt
Managing Context and Memory
CLAUDE.md File
Store project-specific information in CLAUDE.md for persistent context across sessions [66].
- • Project architecture decisions
- • API specifications
- • Coding conventions
- • Environment variables
Conversation History
Claude maintains context within the same session, allowing iterative refinement of requests [68].
- • Follow-up questions
- • Contextual modifications
- • Multiple instance coordination
- • External data integration
Understanding AI Limitations
Security Risks
AI models are optimized for functionality over security and can generate vulnerable code if not properly guided [171].
- • May replicate insecure patterns from training data
- • Can "hallucinate" plausible but incorrect code
- • Lacks deep security understanding
Quality Assurance
Research shows significant percentages of AI-generated code contain vulnerabilities [190].
- • 40% overall vulnerability rate
- • 29.5% for Python code
- • 24.2% for JavaScript code
Critical Requirement: All AI-generated code must undergo thorough human review before deployment
Integrating Claude Code into Development Workflow
Development Workflow Integration
Initial Project Scaffolding
Claude assists in technology stack selection, project structure design, and boilerplate code generation [68].
Feature Development
Rapid feature implementation through natural language descriptions translated to functional code [54, 68].
Automation and Documentation
Task Automation
- Fixing linting issues across multiple files
- Resolving merge conflicts
- Writing boilerplate code
- Generating release notes
Documentation Generation
- Function and class docstrings
- API documentation from code comments
- Architectural overviews
- README file updates
GitHub Actions Integration
Claude Code GitHub Actions enable @claude mentions in PRs and issues for automated code analysis, PR creation, and bug fixing [150].
Instant PR Creation
Generate complete PRs from feature descriptions
Automated Implementation
Turn issues into working code with single commands
Security First
Code remains on GitHub's secure runners
Custom Workflows
Build tailored automation with Claude Code SDK
Comparing Claude Code with Other AI Assistants
Feature Comparison Matrix
| Feature Aspect | Claude Code | ChatGPT | Key Insight |
|---|---|---|---|
| Security Implementation | Comprehensive measures with iterative prompting | Direct but potentially limited initial fixes | Claude requires refinement but delivers broader security features |
| Code Quality | Excellent technical details and best practices | Good functionality focus | Claude beats ChatGPT in developer experience |
| Prompt Responsiveness | Highly responsive to iterative prompting | Direct response to initial prompts | Claude adapts better to refinement and feedback |
| Context Awareness | Project-aware with CLAUDE.md support | Limited to conversation context | Claude maintains better project consistency |
| Hallucination Risk | Present but manageable with review | Similar risk profile | Both require careful double-checking |
[4] Comparison based on security implementation analysis
Security Implementation Analysis
Case Study: Flask API Endpoint Security
In a comparative analysis, both Claude and ChatGPT initially produced code lacking substantial security measures. When prompted to improve security:
ChatGPT Approach
- • Implemented rate limiting directly
- • Focused on single security aspect
- • Less comprehensive solution
- • Direct but limited improvement
Claude Approach
- • Initially implemented HMAC (misaligned)
- • Required specific guidance/nudging
- • Eventually delivered comprehensive solution
- • Included multiple security layers
Final Result: After iterative prompting, Claude implemented input sanitization, rate limiting, HTTPS enforcement, and security headers, demonstrating superior capability when properly guided [4, 428].
Key Comparison Takeaways
Claude Advantages
Better developer experience, comprehensive solutions with iterative prompting, project-aware context
Shared Challenges
Both can hallucinate confidently, require human review, and depend heavily on prompt quality
Best Approach
Use Claude for comprehensive development with iterative refinement and thorough human oversight
Practical Examples and Case Studies
Case Study: Securing a Flask Login Endpoint
⚠️ Insecure Implementation
- • Weak MD5 password hashing
- • Hardcoded credentials
- • No input validation
- • Missing CSRF protection
- • No rate limiting
✅ Claude-Secured Implementation
- • bcrypt password hashing
- • Flask-WTF form validation
- • Rate limiting (5 attempts/minute)
- • CSRF token protection
- • Secure session management
Process: Claude identified vulnerabilities and recommended specific security improvements including Werkzeug's secure password hashing, Flask-Limiter for rate limiting, and Flask-Login for secure session management [106, 109].
SQL Injection Prevention
Vulnerable Code
Secure Alternative
Claude recommends using ORM or parameterized queries to prevent SQL injection [76, 88].
XSS Protection
Risky Rendering
Secure Rendering
Claude suggests using proper templating with automatic escaping and implementing CSP headers [255, 92].
Secure Code Generation Examples
User Registration Endpoint
- • Form validation with CSRF protection
- • Secure password hashing
- • Parameterized database operations
Protected API Endpoint
- • JWT authentication
- • Rate limiting
- • Authorization checks
- • Input validation
Key Insight: The quality of generated code depends heavily on prompt specificity. Detailed security requirements in prompts lead to more robust implementations [4, 404].
Key Takeaways and Recommendations
Strengths of Claude Code
- Comprehensive security implementation with proper guidance
- Project-aware context and CLAUDE.md integration
- Excellent developer experience and best practices
- Responsive to iterative prompting and feedback
Critical Requirements
- Specific, security-focused prompting essential
- Thorough human review of all AI-generated code
- Iterative refinement process necessary
- Security expertise still required for oversight
Strategic Implementation Approach
Claude Code represents a powerful tool for enhancing web application development security and efficiency. However, success depends on treating it as a sophisticated assistant rather than an autonomous developer.
Developer Education
Train developers in effective prompting and security awareness
Process Integration
Establish clear workflows for AI-assisted development
Quality Assurance
Maintain rigorous review processes for all AI-generated code
By combining Claude Code's capabilities with human expertise and robust processes, teams can achieve significant productivity gains while maintaining and even improving code quality and security standards.